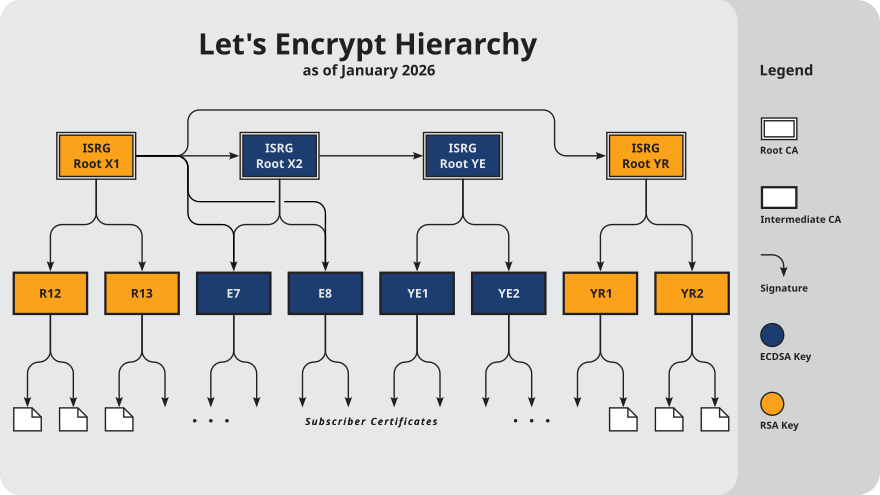
Chains of Trust
This page describes all of the current and relevant historical Certification Authorities operated by Let’s Encrypt. Note that a CA is most correctly thought of as a key and a name: any given CA may be represented by multiple certificates which all contain the same Subject and Public Key Information. In such cases, we have provided the details of all certificates which represent the CA. If you’re looking for the Trust Anchor IDs associated with these CAs, see our page on Object Identifiers.
Root CAs
Our root key material is kept safely offline. We issue end-entity certificates to subscribers from the intermediates described in the next section. All root certificate Subjects have a Country field of C = US.
Note that Root CAs don’t have expiration dates in quite the same way that other certificates do. Although their self-signed certificates do contain a notAfter date, Root Programs and Trust Stores may decide to trust a Root CA beyond that date, or terminate trust in it before that date. As such, the end-of-validity dates given below are approximate, based on current Root Program policies.
- ISRG Root X1
- Subject:
O = Internet Security Research Group, CN = ISRG Root X1 - Key type:
RSA 4096 - Trusted until: 2030-06-04 (generated 2015-06-04)
- CA details: crt.sh, issued certs
- Certificate details (self-signed): crt.sh, der, pem, txt
- Certificate details (cross-signed by DST Root CA X3): crt.sh, der, pem, txt (retired)
- CRL hostname:
x1.c.lencr.org - Test websites: valid, revoked, expired
- Subject:
- ISRG Root X2
- Subject:
O = Internet Security Research Group, CN = ISRG Root X2 - Key type:
ECDSA P-384 - Trusted until: 2035-09-04 (generated 2020-09-04)
- CA details: crt.sh, issued certs
- Certificate details (self-signed): crt.sh, der, pem, txt
- Certificate details (cross-signed by ISRG Root X1): crt.sh, der, pem, txt
- Certificate details (second cross-sign by ISRG Root X1): crt.sh, der, pem, txt
- CRL hostname:
x2.c.lencr.org - Test websites: valid, revoked, expired
- Subject:
These roots are not yet included in Root Program Trust Stores, but will be submitted for inclusion soon:
- ISRG Root YE
- ISRG Root YR
For additional information on the compatibility of our root certificates with various devices and trust stores, see Certificate Compatibility.
Subordinate (Intermediate) CAs
We currently maintain eight intermediates in active rotation. Subscriber certificates containing an ECDSA public key will be issued from one of the ECDSA intermediates; similarly, Subscriber certificates containing an RSA public key will be issued from one of the RSA intermediates. Subscriber certificates issued under the “classic” and “tlsclient” profiles will be issued from one of the first four intermediates listed (E7 through R13); conversely, Subscriber certificates issued under the “tlsserver” and “shortlived” profiles will be issued from one of the latter four intermediates (YE1 through YR2).
All intermediate certificate Subjects have a Country field of C = US.
- Let’s Encrypt E7
- Subject:
O = Let's Encrypt, CN = E7 - Key type:
ECDSA P-384 - Valid until: 2027-03-12
- CA details: crt.sh, issued certs
- Certificate details (signed by ISRG Root X2): crt.sh, der, pem, txt
- Certificate details (cross-signed by ISRG Root X1): crt.sh, der, pem, txt
- CRL hostname:
e7.c.lencr.org - Chains:
- EE ← E7 ← ISRG Root X1 (Default)
- EE ← E7 ← ISRG Root X2
- Subject:
- Let’s Encrypt E8
- Subject:
O = Let's Encrypt, CN = E8 - Key type:
ECDSA P-384 - Valid until: 2027-03-12
- CA details: crt.sh, issued certs
- Certificate details (signed by ISRG Root X2): crt.sh, der, pem, txt
- Certificate details (cross-signed by ISRG Root X1): crt.sh, der, pem, txt
- CRL hostname:
e8.c.lencr.org - Chains:
- EE ← E8 ← ISRG Root X1 (Default)
- EE ← E8 ← ISRG Root X2
- Subject:
- Let’s Encrypt R12
- Let’s Encrypt R13
- Let’s Encrypt YE1
- Subject:
O = Let's Encrypt, CN = YE1 - Key type:
ECDSA P-384 - Valid until: 2028-09-02
- CA details: crt.sh, issued certs
- Certificate details: der, pem, txt
- CRL hostname:
ye1.c.lencr.org - Chains:
- EE ← YE1 ← Root YE ← ISRG Root X2 ← ISRG Root X1 (Default)
- EE ← YE1 ← Root YE ← ISRG Root X2
- EE ← YE1 ← Root YE
- Subject:
- Let’s Encrypt YE2
- Subject:
O = Let's Encrypt, CN = YE2 - Key type:
ECDSA P-384 - Valid until: 2028-09-02
- CA details: crt.sh, issued certs
- Certificate details: der, pem, txt
- CRL hostname:
ye2.c.lencr.org - Chains:
- EE ← YE2 ← Root YE ← ISRG Root X2 ← ISRG Root X1 (Default)
- EE ← YE2 ← Root YE ← ISRG Root X2
- EE ← YE2 ← Root YE
- Subject:
- Let’s Encrypt YR1
- Subject:
O = Let's Encrypt, CN = YR1 - Key type:
RSA 2048 - Valid until: 2028-09-02
- CA details: crt.sh, issued certs
- Certificate details: der, pem, txt
- CRL hostname:
yr1.c.lencr.org - Chains:
- EE ← YR1 ← Root YR ← ISRG Root X1 (Default)
- EE ← YR1 ← Root YR
- Subject:
- Let’s Encrypt YR2
- Subject:
O = Let's Encrypt, CN = YR2 - Key type:
RSA 2048 - Valid until: 2028-09-02
- CA details: crt.sh, issued certs
- Certificate details: der, pem, txt
- CRL hostname:
yr2.c.lencr.org - Chains:
- EE ← YR2 ← Root YR ← ISRG Root X1 (Default)
- EE ← YR2 ← Root YR
- Subject:
Click below for details on additional intermediates which are not part of the active issuance hierarchy:
Backup
These intermediate CAs have currently-valid certificates, but are not being issued from. We may begin issuing Subscriber certificates from them at any time, without warning.
- Let’s Encrypt E9
- Let’s Encrypt R14
- Let’s Encrypt YE3
- Subject:
O = Let's Encrypt, CN = YE3 - Key type:
ECDSA P-384 - Valid until: 2028-09-02
- CA details: crt.sh, issued certs
- Certificate details: der, pem, txt
- CRL hostname:
ye3.c.lencr.org
- Subject:
- Let’s Encrypt YR3
- Subject:
O = Let's Encrypt, CN = YR3 - Key type:
RSA 2048 - Valid until: 2028-09-02
- CA details: crt.sh, issued certs
- Certificate details: der, pem, txt
- CRL hostname:
yr3.c.lencr.org
- Subject:
Retired
These intermediate CAs are no longer being used to issue Subscriber certificates. Those which still have valid certificates may be producing CRLs.
- Let’s Encrypt E1
- Let’s Encrypt E2
- Let’s Encrypt E5
- Let’s Encrypt E6
- Let’s Encrypt R3
- Let’s Encrypt R4
- Let’s Encrypt R10
- Let’s Encrypt R11
- Let’s Encrypt Authority X1
- Let’s Encrypt Authority X2
- Let’s Encrypt Authority X3
- Let’s Encrypt Authority X4
Chains
When an ACME client downloads a newly-issued certificate from Let’s Encrypt’s ACME API, that certificate comes as part of a “chain” that also includes one or more intermediates. Usually this chain consists of just the end-entity certificate and one intermediate, but it could contain additional intermediates. The idea is that, by presenting this whole chain of certificates to a website visitor’s browser, the browser will be able to validate the signatures all the way up to a root that browser trusts without having to download any additional intermediates.
Sometimes there’s more than one valid chain for a given certificate: for example, if an intermediate has been cross-signed, then either one of those two certificates could be the second entry, “chaining up to” either of two different roots. In this case, different website operators may want to select different chains depending on the properties that they care about the most.
Each of the active intermediates above documents which chain is offered by default, and which (if any) additional chains may be requested by ACME clients. In general, chains which terminate at ISRG Root X1 have the largest size but also the greatest compatibility with older clients. Chains which terminate at ISRG Root X2 (only offered for ECDSA certificates) are smaller, but will only work with clients that have received an update to their trust store after 2022 or so. Chains which terminate at Root YE or Root YR will are not expected to work with any of the major trust stores, as those roots have not yet been incorporated.
Subscribers who wish to use one of the alternate chains can reference their ACME client’s documentation for instructions on how to request the alternate chain (for example, certbot’s --preferred-chain flag).